|
Anti-virus
Anti-virus software scans files on your computer's memory for certain patterns that may indicate the presence of malicious software (13).
Anti-virus technology is built around exterminating already existing viruses, so it is important that you update the software regularly to keep up with newly found viruses and malware patterns (13).
If detected, the software may ask you to clean/remove the malicious file if it hasn't done so by itself (13).
|  (17) (17) |
|
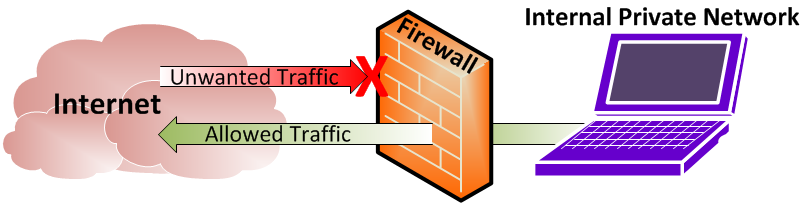
Firewalls
A firewall is a component of network security hardware or software that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules (14).
For a long time, firewalls have been used by companies as a first line of defense for many years, some of them include:
- Proxy Firewalls - A proxy firewall is a network security system that protects network resources by filtering messages at the application layer (15).
- Stateful Inspection Firewalls - Classifies traffic by looking at the destination port and Tracks the state of the traffic by monitoring every interaction of each particular connection until that connection is closed (15).
- Unified Threat Management - Unified Threat Management (UTM) solutions are considered to be the consolidation of stateful inspection firewalls, antivirus, and IPS (Intrusion Prevention System) into a single appliance (15).
|
 (18) (18)
|
 (1)
(1)